Encryption usage by Norwegian online shopping sites (2016 edition)
Over the past several years I have performed occasional surveys of Norwegian shopping sites and their use of encryption. I decided to limit my surveys to Norway, because I concluded that limited knowledge would make collecting a representative international list of foreign shopping sites difficult, and would probably only contain large stores, not small ones.
The last survey I wrote about was performed in early 2015, and while I did not publish an article about it, I did perform a second survey a few months later, in order to get an impression of the effects of some actions initiated after my article. The changes at the time were not significant enough to change what I presented in the previous article, so I did not publish an article discussing those updated results.
A couple of weeks ago the Norwegian Certificate Authority Buypass decided to call attention to the lack of encryption in many online stores, referencing my 2015 article in their press release. After some consideration, I decided that it might be useful to get updated numbers, and performed a new survey of the same sites as in my previous surveys.
Methods
The current list of surveyed sites consists of 205 online stores (the 2015 list had 240 stores; the rest are no longer active). This list has two subgroups:
- Small stores: These 152 stores was originally picked by scanning through a list of stores nominated by customers, maintained by the Norwegian Postal Service.
- Larger stores: The 53 stores in this list consist mainly of large brands and retail chains in Norway, some of which are also major brands in Scandinavia and/or Europe.
When surveying the stores I checked if the following was encrypted:
- front page
- login page
- the shopping cart
- checkout
- whether the entire shopping site was encrypted
I also tested the encryption protocol status of the encrypted pages involved.
I did not complete, and actually stopped well short of completing any transactions as part of this test. In most cases it would not be possible to get close to completing a transaction for the purposes of this survey as many sites require registering an account before a purchase can be completed. The checkout page was usually a log in page, but in the cases where a customer could continue, I did so far enough, if possible, to see which payment options were offered.
A page was considered secure if a padlock was displayed in my browser (Vivaldi 1.5, based on Chromium 54), and unsecure if a padlock was not displayed, whatever the reason. Beside completely unencrypted web pages, there are currently two major reasons for not showing a padlock in Chromium-based browsers: Inclusion of unencrypted content in encrypted pages (mixed security), and forms on a secure page that submit the query to an unencrypted server.
Both of these latter cases were encountered while testing shopping sites, including many checkout pages. One of the cases one might (possibly) consider “amusing” was the “encrypted” version of a shopping site that included a couple of unencrypted images, one of which was of a closed padlock with the text “Secure payments” below.
This method of assessing the security level was chosen because it is what an average security conscius user might rely on; only very advanced users would dig into the details of the web page to discover if the page was “reasonably” secure. It is also the only practical method for a customer to evaluate the security of a site; an encrypted web site may have security problems in the internal systems (and discovering these requires advanced methods, and navigating some murky legal waters), but an unencrypted web site is completely unsecure, by definition.
Results
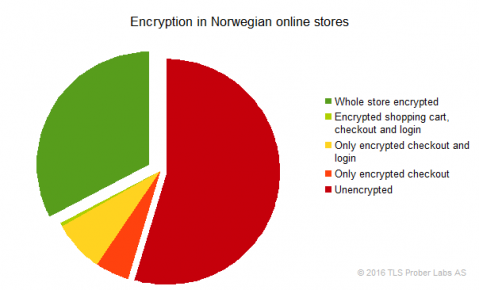
For the entire list, my survey found that
- 33% of surveyed sites store encrypted the entire site, compared to 6% in 2015
- 45% encrypted the checkout process (either a log in page or a page for entering customer information), compared to 30% in 2015
Looking at the corresponding numbers for the two groups of stores reveal a significant difference:
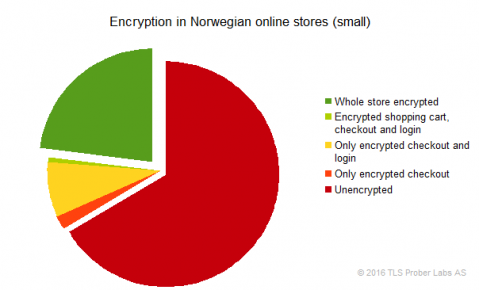
- In this survey, 23% of the small stores encrypted their whole site, and 34% encrypted the checkout, compared to 3% and 21%, respectively, in 2015.
- On the other hand, 60% of the larger stores encrypted the entire store, and 79% the checkout, compared to 17% and 54% in 2015.
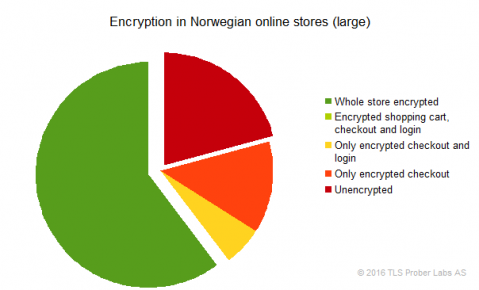
This indicates that the large stores improved the most in use of encryption, particularly compared to my unpublished July 2015 survey.
The results, however, could very easily have been better.
When reviewing some of the unsecure checkout pages, it became clear that the results could easily have been 8 to 10 percentage points better.
Many of the small stores use a hosting provider to host their store and to manage payments. The two largest such providers in my sample are 24Nettbutikk and Mystore. None of the stores using these two providers encrypt their websites (making up 33% of the unencrypted small stores).
75% of the stores hosted by Mystore, however, do use Mystore’s checkout service. This service is served encrypted, but none of the checkout pages using this service were rated as secure, due to the fact that the checkout page included unsecure images from the store as part of the displayed shopping cart.
If Mystore had blocked display of these unsecure images (which I suspect is a 1-10 line fix), the small store segment would have had a 44% coverage of fully encrypted checkout pages, and 53% for all the surveyed stores.
A second category was that at least a couple large stores, the largest of which were the electronics stores Elkjøp and Lefdal had checkout pages that had search forms that submit their queries to an unencrypted server, thus removing the padlock.
If all the stores that mixed secure and unsecure content in the above mentioned fashions had fixed the problems, the large stores would have had 86% encrypted checkout coverage, while the overall result would have been 57%, not 45%.
I do not know whether these results are transferable to other countries. I suspect that the trends in the segments are probably similar to what I am seeing in Norway. My original survey of foreign stores indicated that encryption was more widely used by the foreign stores than the Norwegian ones, but the sites in that survey was mostly large brands, and probably very few, if any small stores, which will make those results difficult to compare with my Norwegian surveys.
Collection of sensitive information
As I detailed in my (Norwegian) 2015 article, the 2015 survey revealed a new issue: Many of the unencrypted checkout pages requested social security numbers as part of new services to complete the purchase using either invoicing or delayed payment (financing). Although the forms for this were, in most cases, inside a frame loaded from a secure server, the fact that this frame was embedded in an unsecure page meant that there was essentially no security protecting the collection.
The Norwegian social security number is a unique identifier assigned at birth (part of the number is your date of birth) and there are strict rules regarding collection and protection of this identifier. Financial institutions are among those required to collect them for all accounts, since they are, among other tasks, used for credit rating and to report information to the tax authorities. For these reasons, obtaining the social security number is a high priority of identity thieves. While not legally considered a sensitive information item about an individual (although I think. in this context, when combined with all the other information collected, it should be considered sensitive), encryption is required for transmission of the number. Not encrypting the collection and transmission of a consumer’s social security number is likely a violation of Norwegian data privacy laws.
In 2015 I found that 26% of the surveyed stores collected the social security number in an unsecure fashion; this year 28% did so. The absolute number of such sites had been reduced slightly, but not enough to actually reduce the percentage, due to the number stores that had shut down since my earlier surveys.
Mystore is one of the providers that host such forms. All of the mixed security checkout pages hosted by Mystore, mentioned above, included a form (from the payment provider Klarna) that could be used to submit the social security number. Had that problem been fixed, the unsecure collection of sensitive information would have been reduced to 20%.
Protocol security
For the most part the SSL/TLS security of these sites is now good. There are, unfortunately, still a couple of POODLEs running around, as well as 10-15% servers with unsecure SSL v3, RC4 and weak Diffie-Hellman configurations, but the numbers are no longer critical. SSL v3 is no longer supported by modern clients, RC4 will soon be equally unsupported. The weak Diffie-Hellman configurations may be the most pressing problem, since those short keys can now be broken relatively quickly, and there are recent indications that a large number of these keys can be even more easily broken, and are used by state actors.
I did notice that most of the secure servers I tested still support Triple-DES (3DES). That is probably not too surprising, since the SWEET32 work that suggest security problems with 3DES is just a few months old, and the current method still require days to gather the necessary data. Based on this, 3DES should probably be retired as soon as possible.
Why is encryption of online shopping sites important?
Properly encrypting data sent between a user and a web site using HTTPS provides three benefits:
- Authentication: The SSL/TLS certificate issued by a recognized Certificate Authority (CA) presented by the server to the browser and then verified assures the browser that it is connecting to the server with the specific hostname in the URL. This will cause the padlock to be displayed in the browser’s address bar. If the web site presents a more advanced (and expensive) Extended Validation (EV) certificate, the browser will also display the company name from the certificate, assuring the user that the web site is owned by a legitimate business, and that it is possible to contact it.
- Privacy: If somebody between you and the web site intercepts your encrypted communication, it is not possible for them to read the clear text of what you send and receive over a properly encrypted connection. Breaking the most advanced encryption methods used today will currently take a very long time.
- Integrity: As part of the encryption, a unique checksum of the encrypted message is calculated and sent to the recipient, and it is checked upon receipt. This prevents an attacker from modifying the encrypted data without it being detected by the recipient.
To put it starkly: If a shopping site is not encrypted, then you don’t know if you are actually communicating with the real site, or with somebody pretending to be the site. There is also nothing preventing anyone (criminals, state actors, your neighbors, or your family) from tracking your activities and create a profile of you. You don’t know if what you ordered is what the shopping site registered, and you don’t know if the payment charged to your credit card was what the web page said you paid, or even that you will receive what was ordered. You won’t find out until you receive the goods and/or the credit card bill. Anyone between you and the shopping site server, especially on public Wi-Fi networks, but your ISP isn’t invulnerable either (and some ISPs have been discovered inserting their own advertisements and cookies in unencrypted web traffic), can read and modify anything sent between you and the site.
If the site is properly encrypted none of these problems can occur normally. The “only” place where problems can develop is on your end and the shopping site’s, since encryption can’t, for example, protect against vulnerabilities in the web site itself; but that is a completely different set of problems, with other solutions.
The reason I am adding the qualifier “properly” above, is that there are many things that need to be done correctly to ensure security of an encrypted connection and web page. All the i’s have to be dotted, and all the t’s crossed, which is why one should get experts to configure and maintain a secure server and web site.
I am emphasizing encryption of the checkout in my surveys because – even though I would prefer the entire store to be encrypted – it is a bit more important that the checkout process is secure, as this involves entering relatively sensitive information; such as name and address, and more sensitive information like credit card details and social security numbers; all of which are of great interest to identity thieves, especially in when provided in a single package.
When part of the checkout process is unencrypted, that means that an active attacker (criminal) can take over the entire session, and fake your entire checkout process, potentially increasing your bill by adding wares to your shopping cart, and even changing the shipping destination. Of course, the same applies to an unencrypted shopping site, even if the checkout is encrypted.
The future for unencrypted online stores
If I should sum up the prospects of unencrypted stores in one word, I think “Bad” fits best.
At present, Google have begun prioritizing results hosted on encrypted servers. This means that shopping sites that do not encrypt the entire site will probably be several pages down the list of search results, rather than near the top, meaning less visitors, and less sales revenue. (Tip to SEO companies: put “Encrypt your site” at the top of the list, if you haven’t already.)
Additionally, within the next few months web browsers will become much more vocal about unencrypted content, as well as unencrypted submission of passwords and credit card details.
Both of these factors means that many customers will never arrive on the site if it is unencrypted, and many of those who do visit might be scared away by the updated browser UI warnings. The result is lower sales, which may ultimately mean closed doors for the store.
In relation to this, it is interesting to note that, of the 35 stores that disappeared since my 2015 survey, only 4 (11%) had an encrypted checkout (another two had mixed security checkouts), and none were using encryption on other parts of the store. It’s probably a co-incidence, but an interesting one.
Looking further ahead, while Google and (possibly) other search engines may only prioritize encrypted content today, I suspect that it won’t be too long until sites with Extended Validation certificates are given an even higher priority, since those certificates ties the content to a specific, legitimate business. Current changes in the media landscape might even hasten such a move, and if so, I suspect social media sites won’t be far behind (if they don’t move first, that is).
Solution: Encrypt everything
If your web store is unencrypted you should immediately upgrade it to be HTTPS-only. My suggestion for small stores is to talk to their designer and hosting service, make sure they have the know-how, then let them handle the details.
While one can go quite some distance with just the inexpensive “Domain Validated” certificates (meaning that only control of the host is checked), I would recommend starting brand-building using the Extended Validation Certificates, too. (Admittedly, some may consider me a bit biased on that point, since I participated in the group that defined how to validate those certificates)
In any case, payment handling should be handled by an experienced payment provider (most stores seem to do this already). This improves security for both the vendor and the customer, and reduces the store’s security exposure since the store will not handle any of the sensitive payment information.
Cost is not likely to be a major issue, although this will depend on the service provider. Extra hardware (or VMs) is seldom necessary, the price for SSL/TLS certificates starts at 0 (zero), and even the more expensive Extended Validation certificates are only a few hundred USD per year.
The end result will be a better and more secure experience for the customer, and hopefully better sales for the store.